In the aftermath of WannaCry, confusion still remains about the origin and impact of ransomware. Yet a little bit of knowledge about the nature of this malicious software could greatly reduce business disruption.
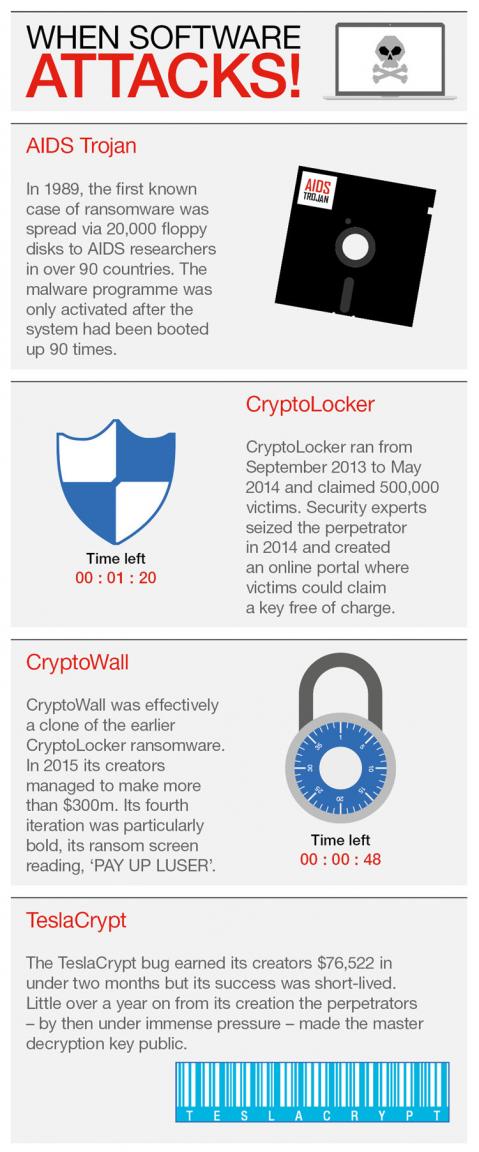
With all the myths and misinformation around ransomware, it’s no surprise that attacks like this year’s WannaCry outbreak are met with panic. More than 150 countries and over 200,000 systems were affected as access to vital data was blocked and ransom payments were demanded in Bitcoins.
With businesses confused about how WannaCry corrupted their system, whether they needed to pay and what steps they should take to get rid of it, our step-by-step explanation reveals how the malicious software finds its way onto a system and what can be done to protect against infection.
So what is ransomware?
Ransomware is a type of cyber-attack where hackers take control of a computer system until a ransom is paid. The perpetrators will usually encourage a victim to click on a link or download what they believe to be a legitimate file. In doing so, the ransomware will lock their files within a network.
‘It’s a software program that is created like any other software program,’ says John Shier, Senior Security Expert at Sophos. ‘Most successful variants of ransomware are written by individuals with a strong programming background.’
Are there different types?
Ransomware takes one of two forms: encryptors block system files and demand a key to unlock the content. Lockers freeze the user out of their operating system completely, making it impossible to not only access the desktop, but apps and files.
Variants can be engineered to behave differently but many share common characteristics such as obscure file names and the outward appearance of a legitimate program or service. Remember that the priority for ransomware is to stay hidden, so undercover launch tactics are built in to avoid detection.
How does it work?
‘Once the ransomware code is running on your machine it will search your folders and sometimes shared volumes for eligible files,’ says Shier. Generally, the eligible files are encrypted using a two-step process. The first uses a randomly generated, unique key that encrypts the files. The second is to use a second key that is unique to your machine to encrypt the rest.
The criminals aren't stealing your files but locking you out of them. ‘It’s like someone sneaking up to your bicycle and attaching a lock to it while you aren’t looking, then demanding payment to remove the lock.
You still have your bike but you can’t use it unless you pay the crook.’
Who does it target?
Over time, emphasis has shifted to focus less on individuals and more on businesses and public institutions.
The reasons are simple: The costs of disruption to a business – whether reputational, financial or legal - are far greater, which means they’re more likely to pay the ransom. The same can be said for public institutions, which harbour huge caches of confidential and valuable information.
How can I recognise it?
The means of infection differs on a case-by-case basis, but typically boils down to one of a handful of mechanisms.
The most popular, and by far the most well-known, are spam email campaigns, which contain either malicious links or attachments. Security exploits in vulnerable software are another popular option. Alternatives, such as websites with embedded malicious code, SMS messaging and self-propagation (from one infected computer to another), are used less frequently.
How big is the problem?
According to Microsoft (external link), the most affected countries were the US, Italy, Russia, Korea and Spain, yet ransomware remains a global problem.
Outbreaks have skyrocketed over the past couple of years, but encounters are beginning to decline due to advances in security software. The figures show that 500 million emails carrying ransomware downloaders are sent every quarter.
Should I ever pay up?
Given that ransomware is spread through social engineering (i.e. psychological manipulation), users should always stay vigilant. General rules of thumb, like steering clear of attachments or links in spam, are a good starting point.
‘Prevention is always preferred when it comes to ransomware,’ says Shier. ‘Paying the criminals for the decryption key should be avoided if at all possible. This simply funds their activities and makes it easier for them to continue spreading ransomware.’
What precautions can I take?
Keep backups of all your data, both on an external hard drive and on the cloud. Bear in mind that when it comes to USBs and external hard drives, you must physically unplug the device after backing up. ‘If your files have been encrypted the best course of action is to restore your files from a previous backup. If the ransomware is done right, there is no way to decrypt the files without the decryption key.’
Smaller adjustments, like ensuring your operating system and software is up to date, changing your browser security and privacy settings and updating plug-ins can make all the difference. Arguably, most important of all is ensuring you have a robust anti-malware solution standing in the way of a potential outbreak.
Finally, once you have restored your files you should run a full system scan to ensure all traces of the ransomware are completely removed from your system.
Learn more about Hiscox Cyber and Data insurance for your clients.